Understanding Cryptography: A Cornerstone of Cybersecurity
Written on
Chapter 1: Introduction to Cryptography
Cryptography is an essential element of cybersecurity, a term that has gained traction across various disciplines. For students in computer science, understanding cryptography is crucial, as it is often a required or elective subject.
This article aims to demystify how secure communication occurs online, particularly through encryption and decryption processes. It is designed for both general readers and those seeking a deeper understanding. While the depth may be limited, it serves as a solid introduction for further exploration.
Section 1.1: Defining Cryptography
Cryptography involves the creation of codes and ciphers, utilizing numbers and letters to obscure messages. In the realm of computer science, it refers to methods for safeguarding communication against various threats.

A security system in computer science is designed to protect data transmitted over communication channels from unauthorized access.
Key Components of Security
A robust security system should encompass three key elements, commonly referred to as the CIA triad:
- Confidentiality: Ensures that sensitive information, like credit card details, is accessible only to authorized entities.
- Integrity: Guarantees that data remains unaltered during transmission, meaning the message received is identical to the one sent.
- Availability: Valid users must have constant access to the services they are entitled to, such as their email accounts.
Section 1.2: The Mechanics of Cryptography
Cryptography employs mathematical algorithms to transform messages into a form that is unreadable to anyone without the proper key, making it difficult to decode.

A fundamental component of cryptography is the cipher model, which facilitates secure communication between a sender and a receiver through encryption techniques.
Elements of a Cipher Model
- Plaintext (X): The original message to be transmitted.
- Key (K): The secret used for encryption and decryption.
- Cipher Text (Y): The encrypted message.
- Algorithm (E or D): The process used for encryption and decryption.
Encryption and Decryption Processes
Encryption converts plaintext to ciphertext using a key, while decryption reverses this process. Mathematically, these processes are represented as:
- Encryption: ( Y = E(X, K) )
- Decryption: ( X = E(Y, K) )
In summary, every message sent over secure channels undergoes encryption before transmission and decryption upon receipt, ensuring privacy.
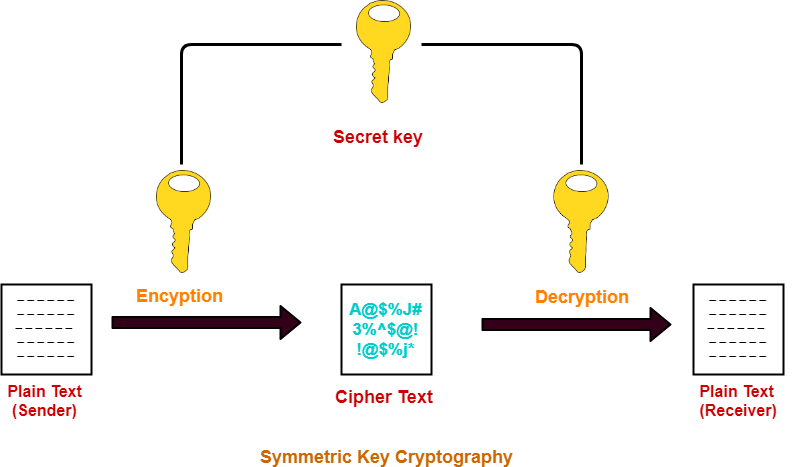
Key Types
Cryptography employs two main key types: Public Keys, which are accessible to everyone, and Private Keys, which remain confidential to authorized users.
Chapter 2: Cryptographic Attacks and Number Theory
This video provides a comprehensive overview of cryptography, covering definitions, algorithms, and the significance of number theory in cryptographic practices.
This full course on cryptography dives deeper into various topics, including encryption methods and practical applications.
Types of Attacks
Cryptanalysis involves attempts to decipher encrypted data, while brute force attacks systematically test every possible key combination to break encryption.
The Role of Number Theory
Number theory, a branch of mathematics focused on integers, underpins many cryptographic methods. It serves as a foundation for various applications in computer science and is essential for understanding cryptography.

Chapter 3: Classification of Cryptographic Techniques
Cryptography can be categorized based on key types and algorithms:
- Symmetric Key Cryptography: Utilizes a single key for both encryption and decryption, offering speed.
- Asymmetric Key Cryptography: Employs a pair of keys (public and private) for secure communication, which is more complex.
RSA Key Exchange Algorithm
The RSA algorithm facilitates secure key exchanges, where the public key is shared openly, while the private key remains confidential. This method is vital for secure communications.
Cryptographic Techniques
- Substitution Techniques: Replace elements of plaintext with other symbols or characters.
- Transposition Techniques: Rearrange the symbols without substitution.
Various substitution techniques include the monoalphabetic and polyalphabetic ciphers, each differing in complexity and security.
Stream and Block Ciphers
Encryption methods are further divided into stream ciphers, which process one bit at a time, and block ciphers, which encrypt data in fixed-size blocks.

Advanced Encryption Standards
The Advanced Encryption Standard (AES) is one of the most secure encryption methods in use today, characterized by its speed and reliability.
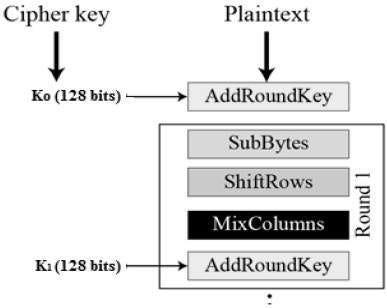
The Data Encryption Standard (DES) and International Data Encryption Algorithm (IDEA) are also notable encryption techniques widely implemented in various applications.
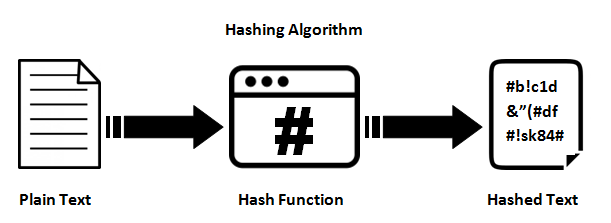
Hash Functions
Hash functions convert messages into fixed-size hash values, ensuring data integrity and security.
Digital Signatures and Certificates
Digital signatures authenticate the identity of users online, providing a unique and secure means of verification. Digital certificates, issued by certification authorities, further enhance trust in online communications.

Conclusion
Cryptography is a rapidly evolving field. Techniques that are secure today may become obsolete tomorrow. Staying informed and adapting to advancements is crucial for anyone involved in cybersecurity.
For those studying this subject, a basic understanding of mathematics and computer science is sufficient. Expect a range of question types, from theoretical explanations to practical applications involving various ciphers.