Innovative Startups Shaping the Future of Enterprise Authorization
Written on
The Growing Need for Enhanced Security
In the coming decade, the demand for advancements in enterprise security systems is set to surge significantly. Currently, the enterprise security landscape faces numerous challenges, prompting the emergence of startups that offer innovative solutions. Among the most fascinating areas to watch is the evolution of authorization technologies.

Cybersecurity Costs on the Rise
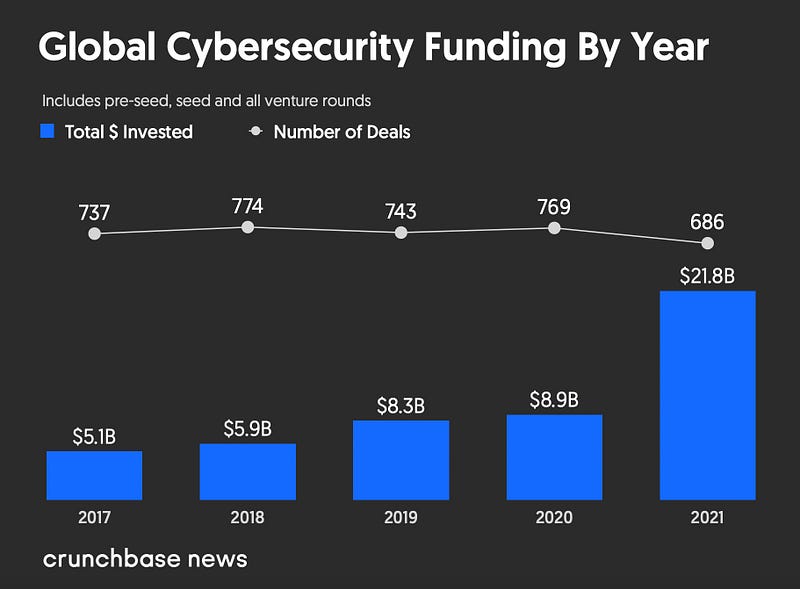
With cyberattacks becoming increasingly detrimental, the financial impact has escalated. For instance, the average cost of a data breach rose from $3.86 million in 2020 to $4.24 million in 2021. As a response, venture capital firms are adapting to the heightened need for robust security measures. In 2021, cybersecurity venture funding reached an unprecedented $21.8 billion, a stark contrast to the approximate 40% of that figure in 2020. The primary focus areas in cybersecurity include identity security, network security, and endpoint security.
Global Identity and Access Management (IAM)
One of the most compelling sectors within cybersecurity is Global Identity and Access Management (IAM). This crucial practice enhances control over user access by identifying, authenticating, and authorizing users while blocking unauthorized access. IAM streamlines access management processes, thus improving overall operational efficiency.
Market Outlook and Growth Prospects
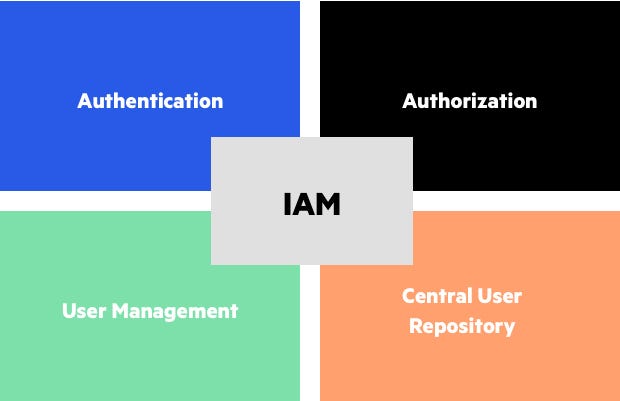
The Global IAM market is anticipated to grow at a compound annual growth rate (CAGR) of 14.5%, expanding from $13.4 billion in 2021 to $34.5 billion by 2028. IAM encompasses various aspects, including user rights management, software architecture, and operational handling for businesses of all sizes. The market is segmented into four key areas: authentication, authorization, user management, and a central user repository. These segments are intricately connected, with the authorization software sector poised to benefit significantly from this growth.
The Challenge of User Permissioning
The automation of user permissions represents a burgeoning opportunity in the authorization field. Building a product, particularly a Software as a Service (SaaS) offering, presents numerous challenges in managing user access. As companies scale, they face complex permissioning issues involving various user types and roles, both internally and externally.
The difficulties of user permissioning stem from several factors:
- Significant backend and frontend development effort is required.
- Resources are diverted from product development and engineering.
- A dedicated security team is necessary to maintain the integrity of the permissioning infrastructure.
As organizations grow, they must allocate considerable time, money, and effort to manage permissions effectively. According to Cerbos, a promising startup in this domain, the hurdles include ongoing maintenance costs, evolving business requirements, and the non-core nature of authorization for many teams.
Automation Trends in IAM
A noteworthy trend is the increasing automation of authorization processes. Numerous APIs are emerging to help product and engineering teams tackle their challenges, enhancing operational efficiency. These automated systems allow businesses to allocate resources towards other priorities, alleviating the burden of maintaining authorization controls. This not only leads to cost savings but also boosts morale among developers by reducing the time spent on permissioning tasks. Teams can create tailored workflows, providing flexibility in user permissions management.
The Rising Stars in Authorization Startups
Opal | Stage: Seed | Backed by: Greylock Partners, Evan Reiser, Andrew Peterson, and Tim Junio
Opal integrates permissioning automation with customizable workflows, enabling employees to efficiently navigate software resources and share responsibilities within their teams.
Cloudentity | Stage: Series A | Backed by: Forgepoint Capital, WestWave Capital
Cloudentity allows organizations to monitor APIs, establish custom workflow policies, and maintain comprehensive reporting and auditing dashboards.
Cerbos | Stage: Seed | Backed by: Connect Ventures, Hello World, and others
Cerbos offers a self-hosted solution for user permissions, granting companies full control over their authorization processes while accommodating intricate requirements.
Ory | Stage: Series A | Backed by: Insight Partners, In-Q-Tel, and Balderton Capital
Ory specializes in low-latency and high-availability authorization solutions, catering to large enterprises that require rapid data processing.

Conclusion: The Future of Authorization
Opal.dev exemplifies an exciting next-generation authorization platform, facilitating just-in-time access and offering actionable insights into user access reviews. With a strong technical foundation and a successful seed funding round from Greylock in late 2021, Opal is well-positioned for future growth in the enterprise sector.
Prominent Entrepreneurs in the Field
Key figures leading the charge in next-generation authorization include Stephen Cobbe and Jan Hellmich (Opal), Jason Needham and ?ukasz Jaromin (Cloudentity), Emre Baran and Charith Ellawala (Cerbos), and Aeneas Rekkas and Thomas Aidan Curran (Ory).
Many other emerging startups and entrepreneurs are making strides in authorization. If you're interested in discovering more about this dynamic field or wish to discuss B2B and enterprise software, feel free to reach out!
By Manan Modi | Twitter | LinkedIn | Contact